Author: TechnoHerder
Kali – Changing Java
There are many types that a tester will need to change the version of Java they are using to match their target. Luckily, there is an easy way to switch between them using DebianAlternatives. The following is an example to install and use an older version of Java. Start by downloading an older version and […]
PostgreSQL – 5432 – TCP
Login into postgres -U user-h host-d database \l – list databases\c [DataNase Name] – connect to database\dt – list datatables\q – quit/exit program\du – list users List of roles Role name Attributes postgres Superuser, Create role, Create DB, Replication, Bypass RLS webapp Superuser SELECT current_setting(‘is_superuser’); Auth Trust Open the file […]
Web Attack Notes
Server-Side Template Injection A certificate is self-signed if the subject and issuer match. CSV Injection And the following one which will take data from cells c1 and c20 and send it to a server/port under your control: XXE Password Tests Insufficient Input Validation JavaScript Unicode Values PostgreSQL Prototype Pollution XSS Cross-Origin Resource Sharing Test SQLi […]
AWS Tools Cheatsheet
Enumerate IAM https://github.com/andresriancho/enumerate-iam ScoutSuite https://github.com/nccgroup/ScoutSuite More Useful Commands
Web Tools Cheatsheet
TestSSL https://github.com/drwetter/testssl.sh SSLyze https://github.com/nabla-c0d3/sslyze Smuggler https://github.com/defparam/smuggler OpenSSL https://github.com/openssl/openssl SSLScan https://github.com/openssl/openssl YAWAST https://github.com/adamcaudill/yawast SQLMap https://github.com/sqlmapproject/sqlmap Tamper scripts MSSQL: tamper=between,charencode,charunicodeencode,equaltolike,greatest,multiplespaces,nonrecursivereplacement,percentage,randomcase,securesphere,sp_password,space2comment,space2dash,space2mssqlblank,space2mysqldash,space2plus,space2randomblank,unionalltounion,unmagicquotes MySQL: tamper=between,bluecoat,charencode,charunicodeencode,concat2concatws,equaltolike,greatest,halfversionedmorekeywords,ifnull2ifisnull,modsecurityversioned,modsecurityzeroversioned,multiplespaces,nonrecursivereplacement,percentage,randomcase,securesphere,space2comment,space2hash,space2morehash,space2mysqldash,space2plus,space2randomblank,unionalltounion,unmagicquotes,versionedkeywords,versionedmorekeywords,xforwardedfor General Tamper testing: tamper=apostrophemask,apostrophenullencode,base64encode,between,chardoubleencode,charencode,charunicodeencode,equaltolike,greatest,ifnull2ifisnull,multiplespaces,percentage,randomcase,space2comment,space2plus,space2randomblank,unionalltounion,unmagicquotes NoSQLMap ClickJacking Change opacity to 0.0001 for malicious intent: Gobuster https://github.com/OJ/gobuster Dirsearch https://github.com/maurosoria/dirsearch Wfuzz https://github.com/xmendez/wfuzz dnscaa https://github.com/weppos/dnscaa Follow these instructions to install dnscaa: Malicious PDF Generator https://github.com/jonaslejon/malicious-pdf Usage Output will be […]
Force NTLM Privileged Authentication
SharpSystemTriggers SharpSystemTriggers is a collection of remote authentication triggers coded in C# using MIDL compiler for avoiding 3rd party dependencies. Spooler Service Abuse If the Print Spooler service is enabled, you can use some already known AD credentials to request to the Domain Controller’s print server an update on new print jobs and just tell […]
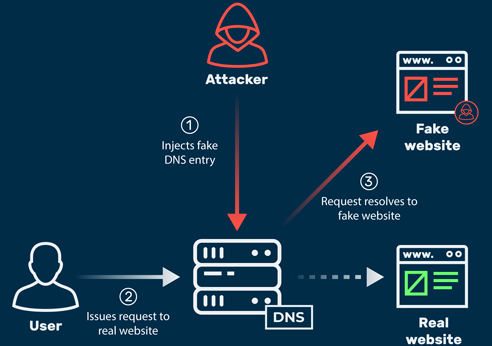
Spoofing LLMNR, NBT-NS, mDNS/DNS and WPAD and Relay Attacks
Network protocols LLMNR, NBT-NS, and mDNS Microsoft systems use Link-Local Multicast Name Resolution (LLMNR) and the NetBIOS Name Service (NBT-NS) for local host resolution when DNS lookups fail. Apple Bonjour and Linux zero-configuration implementations use Multicast DNS (mDNS) to discover systems within a network. These protocols are unauthenticated and broadcast messages over UDP; thus, attackers […]
SSH – 22 – TCP
Basic Information SSH or Secure Shell or Secure Socket Shell, is a network protocol that gives users a secure way to access a computer over an unsecured network.Default port: 22 SSH servers: SSH libraries (implementing server-side): Enumeration Banner Grabbing Automated ssh-audit ssh-audit is a tool for ssh server & client configuration auditing. https://github.com/jtesta/ssh-audit is an […]
rpcclient – 135 – TCP/UDP
What is a RID A Relative Identifier (RID) is a unique identifier (represented in hexadecimal format) utilized by Windows to track and identify objects. To explain how this fits in, let’s look at the examples below: Definition from here. Enumeration with rpcclient Pat of this section was extracted from book “Network Security Assesment 3rd Edition“You […]