Adding Additional Port Forwards During Existing Session
A little trick to setup further port forwards within a current SSH session is to press “<shift> <enter> ~ c” simultaneously and then supply the relevant command.
Setting Up Multiple RDP Connections
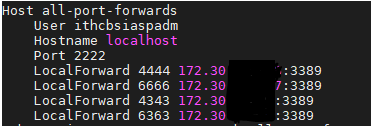
On the AWS box (connecting to deployed Kali):
Edit the AWS instance .ssh/config to set up port forwards to access internal targets RDP:
Host all-port-forwards
User ithcbsiaspadm
Hostname localhost
Port 2222
LocalForward 4444 172.30.xxx.xxx:3389
LocalForward 6666 172.30.xxx.xxx:3389
LocalForward 4343 172.30.xxx.xxx:3389
LocalForward 6363 172.30.xxx.xxx:3389
Connect to the deployed Kali instance to establish all port forwards:
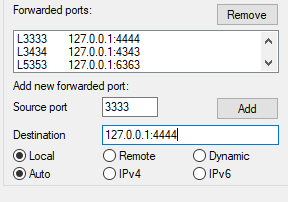
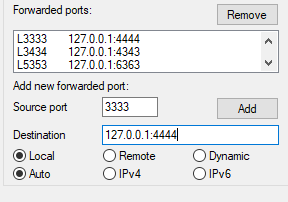
Connect to each of the established port forward using Putty (Our host to AWS):
Note: Mobaxterm free is limited to 3 tunnels
1. Configure the usual ssh connection settings
2. Configure multiple forwards via Putty (connecting to previous forwards)
You will then be able to establish a connection to each target via built in Windows RDP on the local source port (on your Windows host):
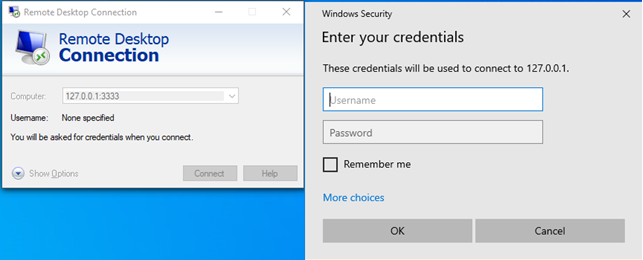
This will connect to 4444 on the Local Forward on the AWS .ssh/config.