Rooting Android & Jailbreaking iOS
Android
It is recommended to use an android device to test the application. If you cannot get one, then you can use an Android VM.
Alternatively, you can configure an Android device. There are lots of guides on the Internet to root an Android device.
A guide for Google Pixel rooting is:
https://hack.technoherder.com/rooting-android/
For this guide, I have rooted a Xiaomi Redmi S2 using Magisk and TWRP.
Steps:
- Enable developer options (Settings > About phone – tap on version a few times).
- Go to developer options (Settings > Additional Settings >Developer options).
- Enable USB debugging. In most Android devices, you can activate the USB debugging directly. In Xiaomi devices, you need to unlock the Bootloader first. To do this, enable “OEM Unlocking” and “USB debugging” first. Then go to “Mi Unlock status” and add a Mi account (you need a SIM card with Internet access to do this).
- Connect the device to your laptop and download Fastboot and the TWRP image of your device.
- Download Magisk and add the zip to the device’s storage.
- Put your device in fastboot mode (power button + volume down button).
- Open a CMD and run the following commands to install the TWRP image on your device:
fastboot flash recovery recovery.img fastboot boot recovery.img - the last command may never finish, but that is fine, just turn off the device.
- Put your device in recovery mode (power button + volume up button).
- Now touch on “Install” and select the Magisk zip that you added before.
- Reboot the device, and you should be root now.
You can download Root checker to confirm that your device was successfully rooted. Other useful apps are Termux to have a shell on your device and adb Insecure to run adb as root.
iOS
You can check your iOS model and version on https://pangu8.com/jailbreak/. Each model and iOS version has different ways to jailbreak the device.
Some ways require MacOS to jailbreak the iphone/ipad, but most of them can be done using Windows. The easiest way is using Unc0ver. Scroll down to see the guide and follow the steps to install unc0ver and jailbreak the device.
Now you can use Cydia to install all the packages and apps that you need, like A-Bypass, Frida, OpenSSH, etc.
1. Device Communication
Android – ADB Installation
Android Debug Bridge (adb) is a versatile command-line tool that lets you communicate with a device. You can download it as part of the SDK Platform Tools.
Unzip the folder and add it to the PATH so you can run ADB anywhere.
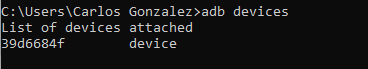
Run adb devices to list all your devices:
iOS- OpenSSH
Communication between your laptop and your iphone/ipad must be done through OpenSSH. You can download it here.
Once you have it installed on your laptop, you have to install the OpenSSH source in Cydia (Search > OpenSSH > Install).
Now you can connect to your device as root using ssh and your device’s IP (IP can be found in Settings > Wifi > info icon > IP Address).The default password is alpine
SSH -p <PORT> root@<ip_address>As a rule of thumb, SSH is listening on port 22. Some jailbreaks (including Meridian and checkra1n) use port 44 instead.
After issuing this command, you can expect one of the three results.
- Connection successful. You’ll gain shell access on the device.
- Connection refused. This can mean that SSH is not installed or the device is not jailbroken. You have to install the package from Cydia or jailbreak the device.
- Permission denied, please try again. SSH is installed, but the default password is not “alpine”. You can reset such passwords (read below for instructions).
You can also use the nmap tool, which will scan the ports on the target device and list services listening on these ports. Use the following command:
nmap -p 1-100 <ip_address> (scans ports 1 to 100)
nmap -p- <ip_address> (scans all ports)2. Frida & Objection Installation
Frida is a dynamic code instrumentation toolkit that is used to hook into the running process of the application and modify the code on the fly without any requirement for re-launching or re-packaging.
Objection is a wrapper for Frida which has some useful functionality.
First you need to install the client on your laptop. Both are python tools and can be installed with pip:
pip install frida-tools
pip install objectionNote: you may need to add to the PATH the Python Scripts path to be able to run these commands anywhere.
Now you need to install the Frida server on your device.
Android
Download the Frida server here: https://github.com/frida/frida/releases
Unzip it and use ADB to put the file on your device:
adb push frida-server /data/local/tmp/Change the permission of the frida-server file and run it in background:
adb shell "chmod 755 /data/local/tmp/frida-server"
adb shell "/data/local/tmp/frida-server &"iOS
Add Frida’s repository to Cydia (Manage > Sources > Edit > Add > https://build.frida.re). Now go to sources, select the Frida source and install the Frida package.
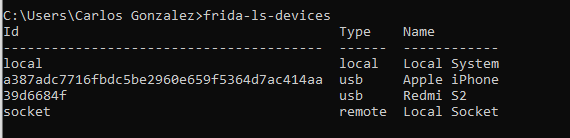
Now you can run frida-ls-services to list all the attached devices:
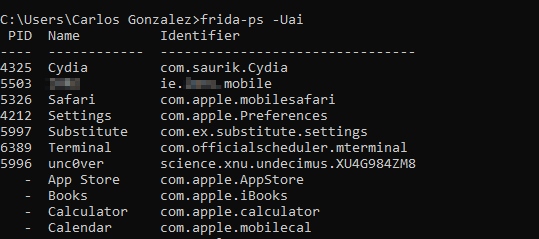
Your installation was successful if you can see the installed applications in the device when you run frida-ps -Uai
SSL-Pinning and Root detection bypass
Most of the applications have SSL-Pinning to prevent Man in the Middle attacks. We need to have this deactivated to use Burpsuite and intercept the requests. Ideally, the client must send us two copies of the application, one with SSL-Pinning and another without it. But if it is not the case, we can try to bypass it using Frida and Objection:
Android:
objection --gadget <app name> explore
android sslpinning disableiOS:
objection --gadget <app name> explore
ios sslpinning disable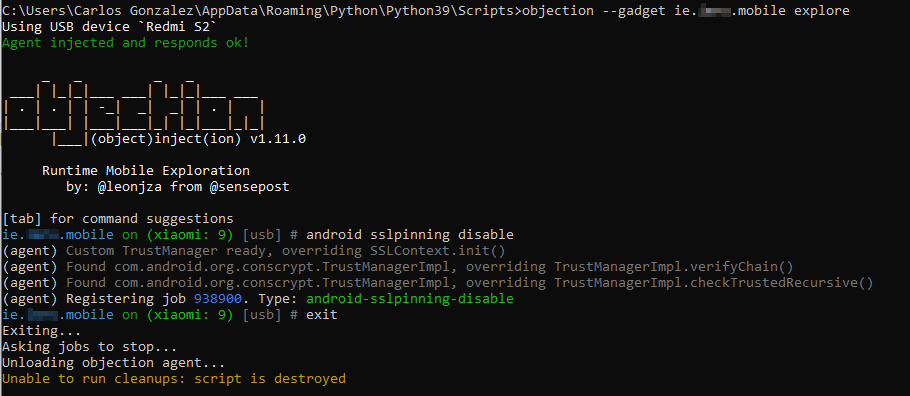
The same thing happens with rooted devices. Some apps try to detect if the device is rooted/jailbroken and if so, they stop. You can use Objection as well using these commands:
objection --gadget <app name> explore
android root disableYou can use Objection as well for iOS, but it requires a few more steps, and I found it easier to bypass the jailbreak detection using the A-Bypass Cydia’s package. Add the source http://repo.co.kr to Cydia and install the A-Bypass tweak. Then go to Settings > A-Bypass and scroll down. Find the application that you want to bypass and mark it.
3. Getting IPA and APK files
You will need the IPA and APK files to do the static analysis. If the client didn’t provide it and you had to install it using Google Play / Apple Store, you can obtain it following these steps:
Android
You can download the apk using adb.
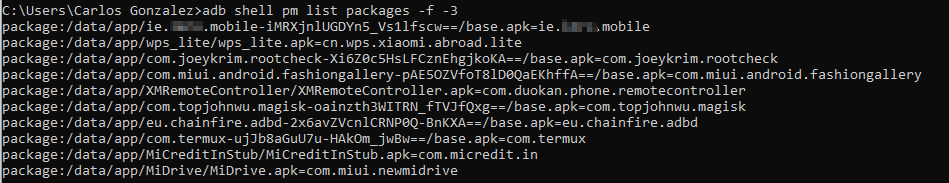
- List the routes to all the applications installed:
adb shell pm list packages -f -3
- Use adb pull to download the apk (note that you don’t have to write the last part of the route):
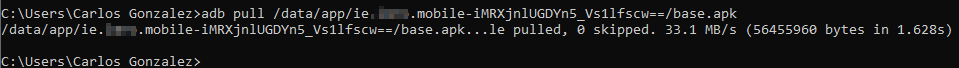
iOS
- Use ssh to open a terminal.
- Go to /var/containers/Bundle/Application
- Find the id of your app using this command: ls * | grep -B 2 -i ‘<app name>’
- Create a folder called “Payload” and copy the .app folder. Then, zip the Payload folder as the IPA file:

cp -r <appName>.app/ Payload/
zip -r /var/root/IPA/appName.ipa Payload/Now you can move your IPA file to your laptop using scp:
scp root@<iphone IP>:/var/root/IPA/appName.ipa appName.ipa4.Reverse Engineering applications
You can decompile an application to see the code and search for hardcoded credentials or dangerous functions:
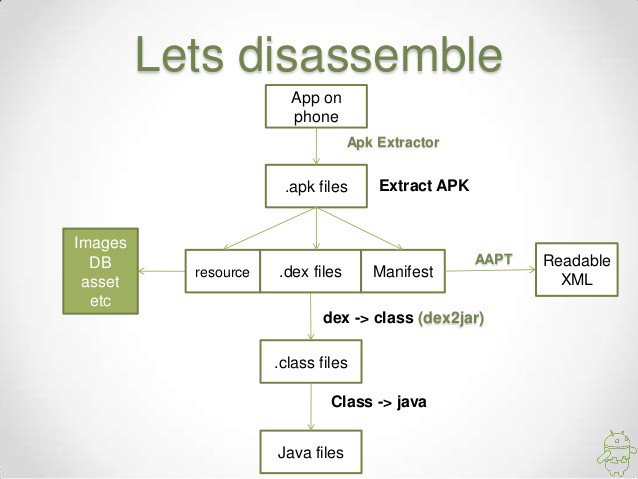
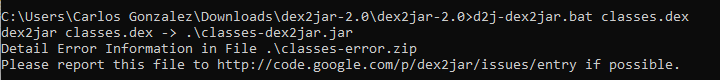
An apk file is just a zipped file with the resources, the .dex files and the Android Manifest. So you can get these files renaming the .apk file to .zip and unzipping it. Then you can use dex2jar to convert the classes.dex file in a .jar:
Finally, you can open this .jar file with jd-gui and see the code.
5. Automated Mobile Application Security Assessment
There are a lot of different tools that you can use to analyze a mobile application. One of the best-known tools is MobSF. You can download the tool (it has some requirements). In Windows and Linux you will be able to do a static analysis of APKs. If you want to analyze an IPA, you will need a mac.
Alternatively, you can use the MobSF live version and upload the IPA/APK. But don’t do this with non-public client applications, because when you upload the file to the web, the analysis data will be public and anyone can see it. Uploading them can be a breach of our clients’ privacy.
6. Intercepting requests with Burpsuite
You can use Burpsuite to intercept the request made by the application. The way I do it is creating a Mobile hotspot on Windows:
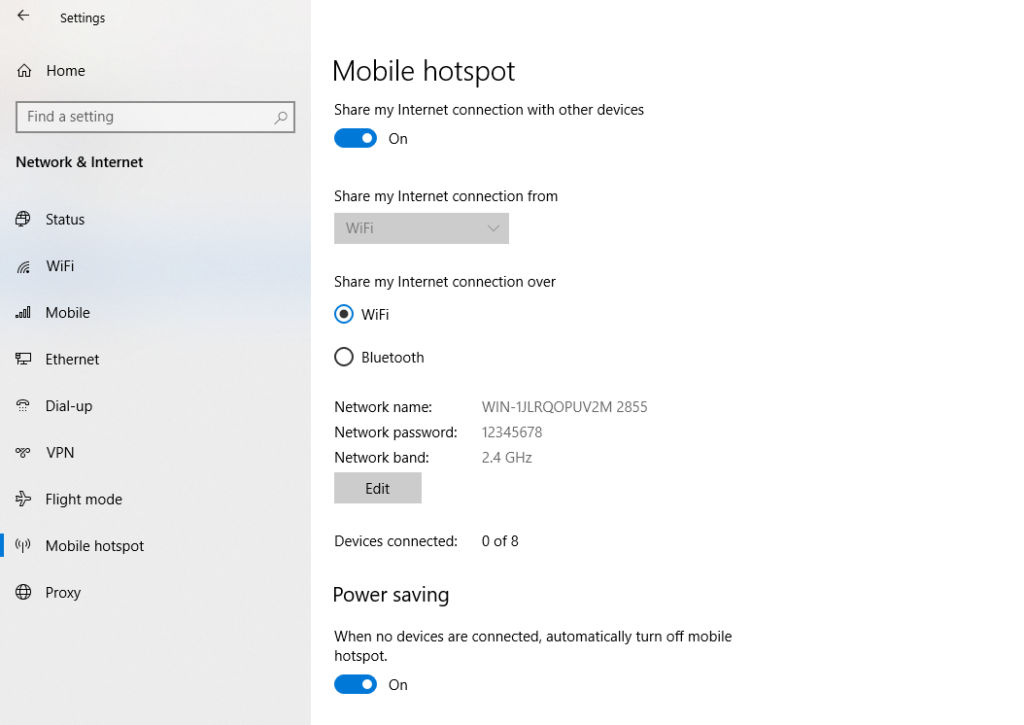
Go to Burpsuite > Proxy > Options and edit the Proxy Listener so it listens to all interfaces.
Connect your device to this wifi, go to the wifi options and configure the proxy as Manual. Put your computer’s IP as the Server, and the listener’s port as the Port. The last step is to download the Burpsuite certificate. You can follow this guide for Android and this one for iOS.
Now you should be able to intercept the requests with Burpsuite.
After all these steps, your environment should be configured and ready to perform a mobile application pentesting.

repo.co.kr
Merona Repository is the fastest place to get the tweak you want.

Releases · frida/frida · GitHub
github.com
Clone this repo to build Frida. Contribute to frida/frida development by creating an account on GitHub.
iOS Jailbreaking [Download now] – Pangu8
pangu8.com
All the iOS jailbreak tools & iOS Hacks are available to download according to your iOS version. Also, find all iOS Jailbreaking / hacking information here